Part 1 - Making your first call to CMS
Part 2 - XMPP and CMA
Part 3 - Integrating Core and Edge
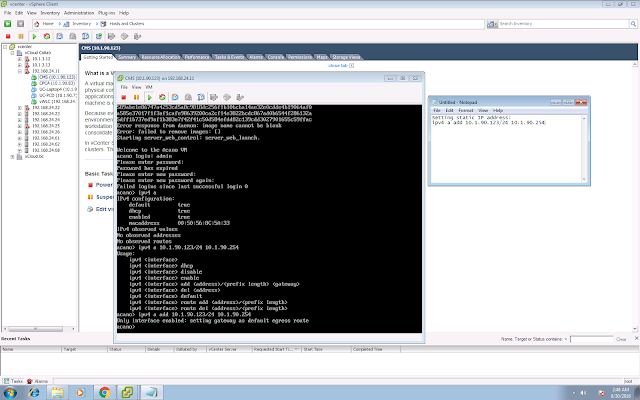
In this post, we are going to deploy a single CMS Core and a single CMS Edge.
1. Certificate for Core and Edge. Like our previous posts in Part 1 and Part 2, I am going to use self signed cert for simplicity.
CMS Core:
pki selfsigned core
CMS Edge:
pki selfsigned edge
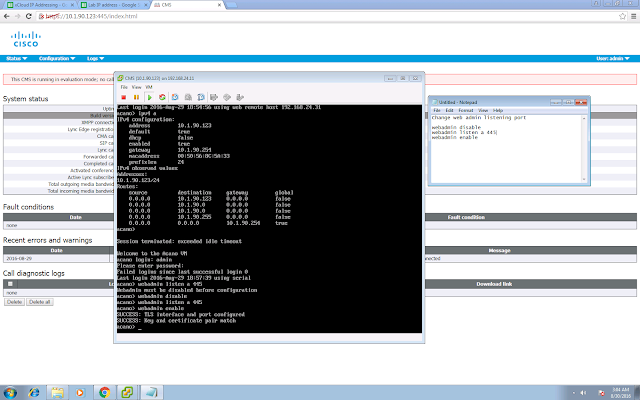
2. Using WinSCP or other SCP / sFTP client, to download the CMS Core certificate, in my case it is core.crt. Copy this Core certificate to Edge using your SCP client.
In CMS Edge, create the loadbalancer service module and config the certificate for authentication. You will need to trust your Core certificate in Edge. In my lab it is a single NIC Edge.
CMS Edge:
loadbalancer auth edge edge.key edge.crt core.crt
loadbalancer trunk edge a:4999
loadbalancer trunk public edge a:5222 lo:5222
loadbalancer enable edge
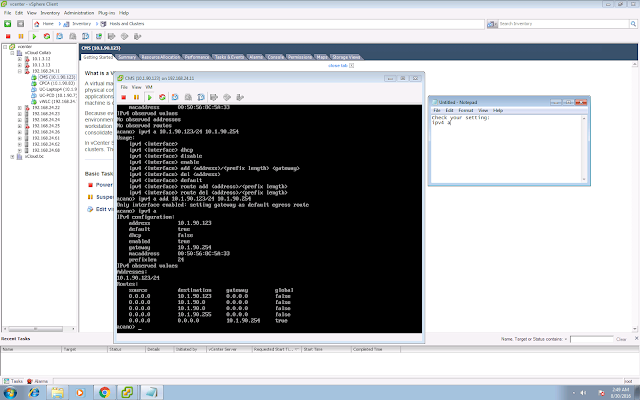
3. In CMS Core, you are required to create a trunk. Similarly, copy the edge certificate to core, you will need to trust the edge certificate in core. 10.1.90.124 is the edge IP address.
CMS Core:
trunk create trunktoedge xmpp
trunk auth trunktoedge core.key core.crt edge.crt
trunk edge trunktoedge 10.1.90.124 4999
trunk enable trunktoedge
You can use the trunk debug trunktoedge (the tag name) to see whether the trunk is up on core.
4. There are a few service modules can be enabled on Edge. If you want to enable SIP Edge, you will need the below command:
CMS Edge:
sipedge public a:5061
sipedge public-ip 1.2.3.4
sipedge private a:3061
sipedge certs sipedge.key sipedge.crt
5. Another service module on Edge is TURN. To enable TURN, you will need the following command:
turn credentials admin admin xcloud-hk.com
turn listen a
turn public-ip 1.2.3.4
turn enable
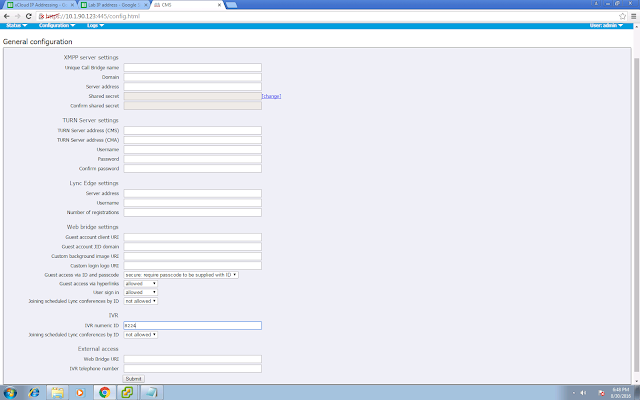
From the web user interface, you can enter the details under "TURN Server settings". TURN Server Address (Server) is the intenal server IP address that the Call Bridge will use to access the TURN server. TURN Server Address (Clients) is the public IP address assigned to the TURN server that external clients will use to access the TURN server.
6. Finally you can enable the webbridge module on Edge, it will allow internal and external participants to join a meeting with their WebRTC capable browser.
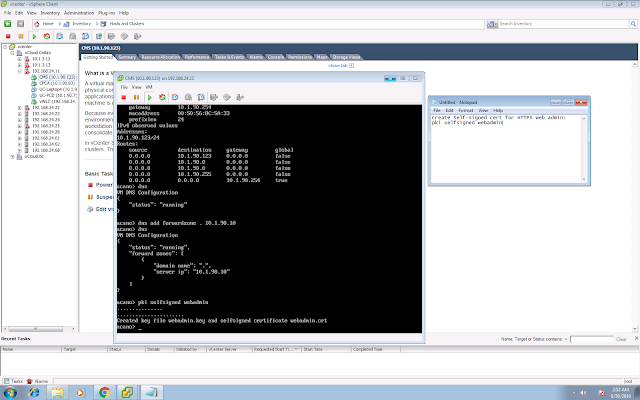
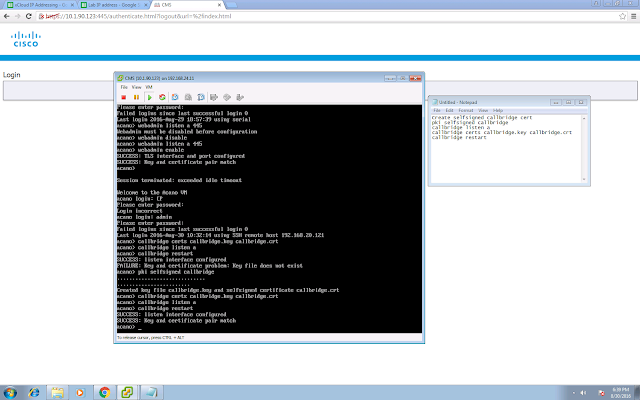
First of all, certificate again.
CMS Edge:
pki csr webbridge CN:webbridge.xcloud-hk.com
pki selfsigned webbridge
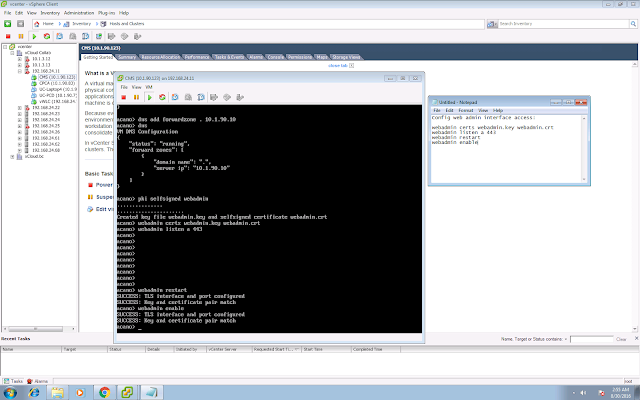
Copy your core CallBridge certificate to Edge, your webbridge service needs to trust your callbridge cert. Then config the webbridge parameters:
webbridge listen a
webbridge certs webbridge.key webbridge.crt
webbridge trust callbridge.crt
webbridge http-redirect enable
webbridge enable
After configured, you can type "webbridge" to check your configured parameters.
Go to Configuration > General, enter your Guest account client URI, for example https://webbridge.xcloud-hk.com. The Guest Account JID domain is your domain, in my case it is xcloud-hk.com
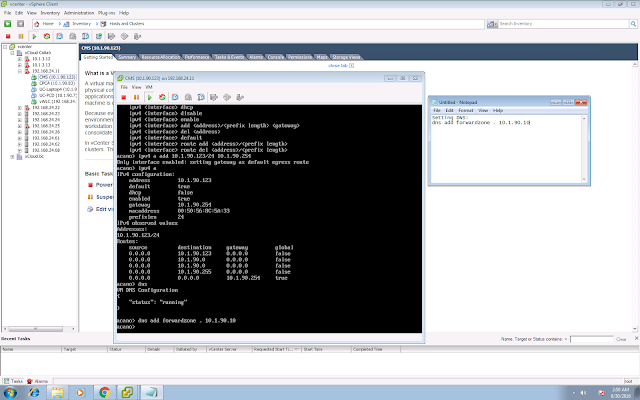
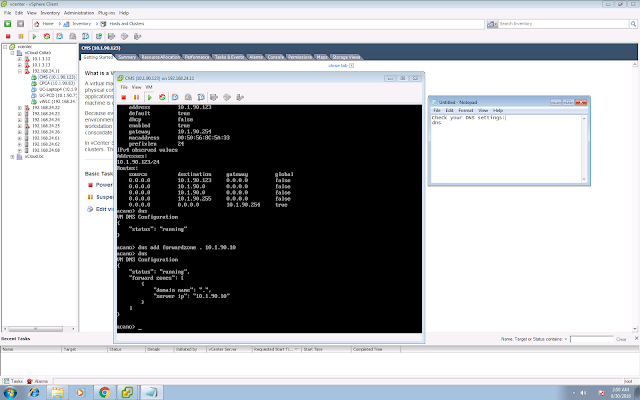
Depends on your DNS settings, you might need a few static entries on your edge, to resolve the xmpp SRV to your local loadbalancer FQDN.
dns add rr "loadbalancer.xcloud-hk.com. IN A 10.1.90.124"
dns add rr "_xmpp-server._tcp.xcloud-hk.com. 86400 IN SRV 0 5 5269 loadbalancer.xcloud-hk.com."
dns add rr "_xmpp-client_tcp.xcloud-hk.com. 86400 IN SRV 0 5 5222 loadbalancer.xcloud-hk.com."
After all these steps, you should be able to use webbridge to join a meeting with WebRTC.
In summary, we have covered the integration between core and edge in a single split deployment, and we can enable a few service modules on edge including SIP Edge, TURN and WebBridge, for different call scenarios especially for B2B calls.
Part 1 - Making your first call to CMS
Part 2 - XMPP and CMA
Part 3 - Integrating Core and Edge
Part 2 - XMPP and CMA
Part 3 - Integrating Core and Edge
In this post, we are going to deploy a single CMS Core and a single CMS Edge.
1. Certificate for Core and Edge. Like our previous posts in Part 1 and Part 2, I am going to use self signed cert for simplicity.
CMS Core:
pki selfsigned core
CMS Edge:
pki selfsigned edge
2. Using WinSCP or other SCP / sFTP client, to download the CMS Core certificate, in my case it is core.crt. Copy this Core certificate to Edge using your SCP client.
In CMS Edge, create the loadbalancer service module and config the certificate for authentication. You will need to trust your Core certificate in Edge. In my lab it is a single NIC Edge.
CMS Edge:
loadbalancer auth edge edge.key edge.crt core.crt
loadbalancer trunk edge a:4999
loadbalancer trunk public edge a:5222 lo:5222
loadbalancer enable edge
3. In CMS Core, you are required to create a trunk. Similarly, copy the edge certificate to core, you will need to trust the edge certificate in core. 10.1.90.124 is the edge IP address.
CMS Core:
trunk create trunktoedge xmpp
trunk auth trunktoedge core.key core.crt edge.crt
trunk edge trunktoedge 10.1.90.124 4999
trunk enable trunktoedge
You can use the trunk debug trunktoedge (the tag name) to see whether the trunk is up on core.
4. There are a few service modules can be enabled on Edge. If you want to enable SIP Edge, you will need the below command:
CMS Edge:
sipedge public a:5061
sipedge public-ip 1.2.3.4
sipedge private a:3061
sipedge certs sipedge.key sipedge.crt
5. Another service module on Edge is TURN. To enable TURN, you will need the following command:
turn credentials admin admin xcloud-hk.com
turn listen a
turn public-ip 1.2.3.4
turn enable
From the web user interface, you can enter the details under "TURN Server settings". TURN Server Address (Server) is the intenal server IP address that the Call Bridge will use to access the TURN server. TURN Server Address (Clients) is the public IP address assigned to the TURN server that external clients will use to access the TURN server.
6. Finally you can enable the webbridge module on Edge, it will allow internal and external participants to join a meeting with their WebRTC capable browser.
First of all, certificate again.
CMS Edge:
pki csr webbridge CN:webbridge.xcloud-hk.com
pki selfsigned webbridge
Copy your core CallBridge certificate to Edge, your webbridge service needs to trust your callbridge cert. Then config the webbridge parameters:
webbridge listen a
webbridge certs webbridge.key webbridge.crt
webbridge trust callbridge.crt
webbridge http-redirect enable
webbridge enable
After configured, you can type "webbridge" to check your configured parameters.
Go to Configuration > General, enter your Guest account client URI, for example https://webbridge.xcloud-hk.com. The Guest Account JID domain is your domain, in my case it is xcloud-hk.com
Depends on your DNS settings, you might need a few static entries on your edge, to resolve the xmpp SRV to your local loadbalancer FQDN.
dns add rr "loadbalancer.xcloud-hk.com. IN A 10.1.90.124"
dns add rr "_xmpp-server._tcp.xcloud-hk.com. 86400 IN SRV 0 5 5269 loadbalancer.xcloud-hk.com."
dns add rr "_xmpp-client_tcp.xcloud-hk.com. 86400 IN SRV 0 5 5222 loadbalancer.xcloud-hk.com."
After all these steps, you should be able to use webbridge to join a meeting with WebRTC.
In summary, we have covered the integration between core and edge in a single split deployment, and we can enable a few service modules on edge including SIP Edge, TURN and WebBridge, for different call scenarios especially for B2B calls.
Part 1 - Making your first call to CMS
Part 2 - XMPP and CMA
Part 3 - Integrating Core and Edge