Haven't update the blog for a while as I was busy at work, study and personal live. During Christmas I want to watch a movie, and I've subscribed Netflix as a result. I assume what I need to do is simply go to the Netflix website and choose the movie that I want, and watch it. However, life is not as simple as you think. I am keep on getting error saying that I have some kind of network connection / proxy issue to prevent me from watching the movie.
After some digging, seems Netflix doesn't like IPv6, especially the setup in my home, where I have my v6 connectivity tunnel through Hurricane Electric. To verify what IPv6 address Netflix is using:
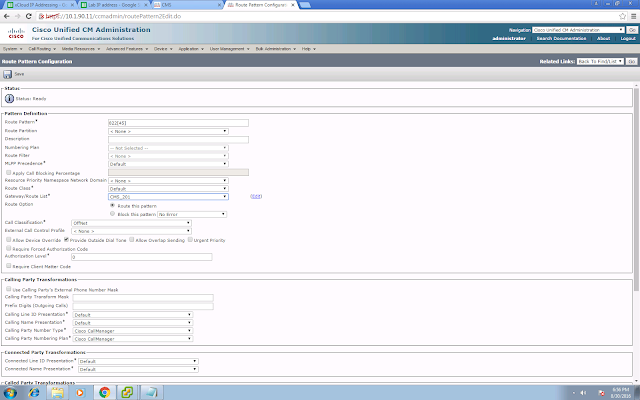
This is the ACL I've implemented in my 1941 router to filter out the IPv6 address block of Netflix. With this workaround I am now able to watch some movies during the festive season!
After some digging, seems Netflix doesn't like IPv6, especially the setup in my home, where I have my v6 connectivity tunnel through Hurricane Electric. To verify what IPv6 address Netflix is using:
$ dig -t AAAA cbp-us.nccp.netflix.com
; <<>> DiG 9.8.3-P1 <<>> -t AAAA cbp-us.nccp.netflix.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- 64879="" id:="" noerror="" opcode:="" query="" span="" status:="">
;; flags: qr rd ra; QUERY: 1, ANSWER: 10, AUTHORITY: 4, ADDITIONAL: 2
;; QUESTION SECTION:
;cbp-us.nccp.netflix.com. IN AAAA
;; ANSWER SECTION:
cbp-us.nccp.netflix.com. 0 IN CNAME cbp-us.nccp.geo.netflix.com.
cbp-us.nccp.geo.netflix.com. 0 IN CNAME cbp-us.nccp.us-west-2.prodaa.netflix.com.
cbp-us.nccp.us-west-2.prodaa.netflix.com. 60 IN AAAA 2620:108:700f::36ba:c314
cbp-us.nccp.us-west-2.prodaa.netflix.com. 60 IN AAAA 2620:108:700f::3270:4b38
cbp-us.nccp.us-west-2.prodaa.netflix.com. 60 IN AAAA 2620:108:700f::340a:2bb5
cbp-us.nccp.us-west-2.prodaa.netflix.com. 60 IN AAAA 2620:108:700f::3695:797a
cbp-us.nccp.us-west-2.prodaa.netflix.com. 60 IN AAAA 2620:108:700f::3645:db3d
cbp-us.nccp.us-west-2.prodaa.netflix.com. 60 IN AAAA 2620:108:700f::3420:816
cbp-us.nccp.us-west-2.prodaa.netflix.com. 60 IN AAAA 2620:108:700f::3459:e8e6
cbp-us.nccp.us-west-2.prodaa.netflix.com. 60 IN AAAA 2620:108:700f::36bb:40b9
;; AUTHORITY SECTION:
prodaa.netflix.com. 68907 IN NS ns-1606.awsdns-08.co.uk.
prodaa.netflix.com. 68907 IN NS ns-1489.awsdns-58.org.
prodaa.netflix.com. 68907 IN NS ns-375.awsdns-46.com.
prodaa.netflix.com. 68907 IN NS ns-749.awsdns-29.net.
;; ADDITIONAL SECTION:
ns-375.awsdns-46.com. 68861 IN A 205.251.193.119
ns-749.awsdns-29.net. 68861 IN A 205.251.194.237
;; Query time: 63 msec
;; SERVER: 218.252.0.24#53(218.252.0.24)
;; WHEN: Sun Dec 25 22:13:54 2016
;; MSG SIZE rcvd: 507
This is the ACL I've implemented in my 1941 router to filter out the IPv6 address block of Netflix. With this workaround I am now able to watch some movies during the festive season!
sh access-list block-netflix
IPv6 access list block-netflix
deny ipv6 any 2620:108:700F::/48 (412 matches) sequence 20
permit ipv6 any any (1804317 matches) sequence 30
interface GigabitEthernet0/1
! My LAN side interface
ipv6 traffic-filter block-netflix in
end