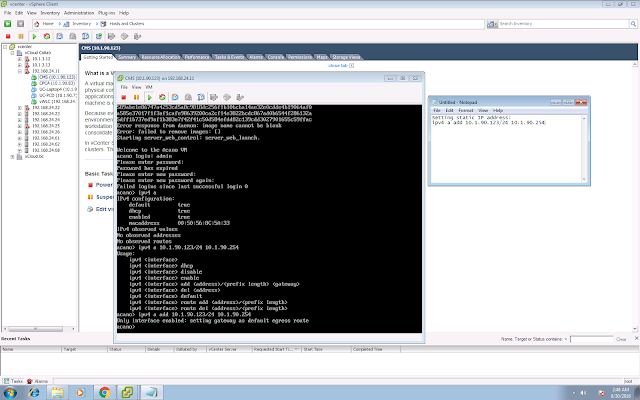
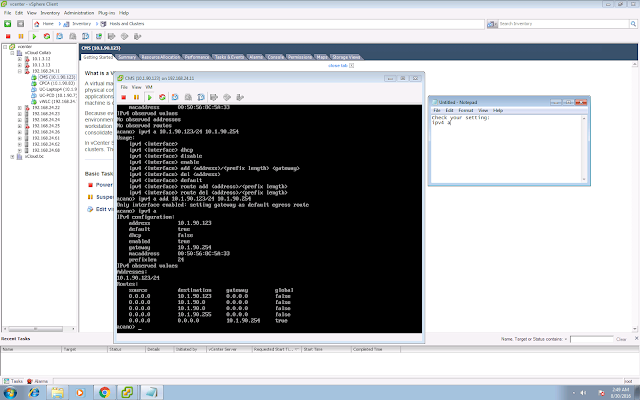
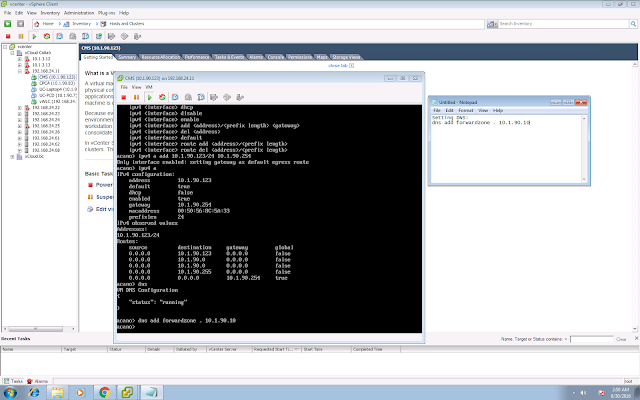
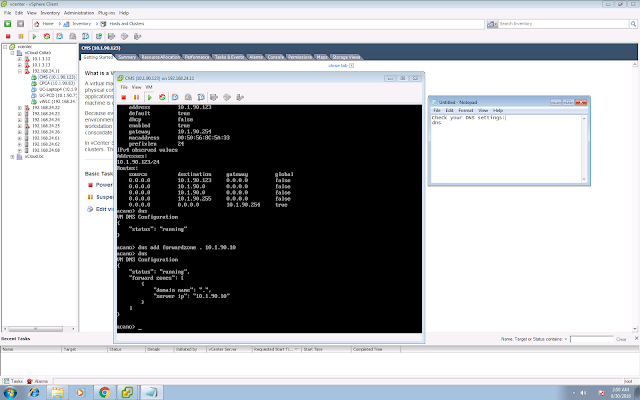
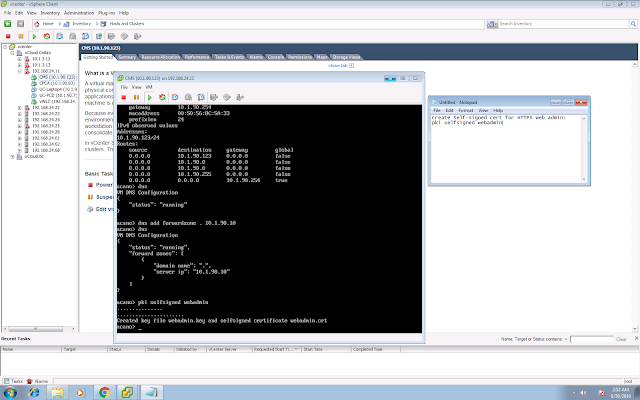
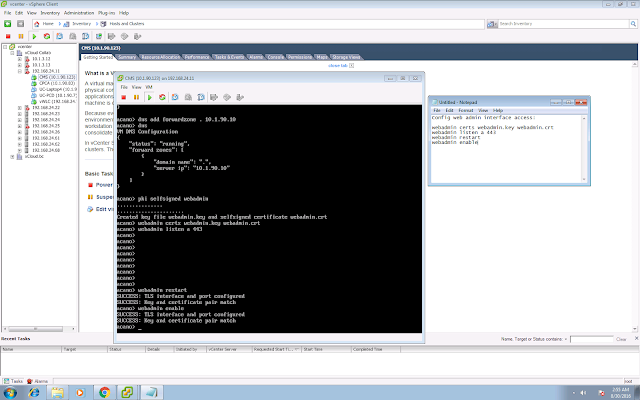
A few EoS/EoL announcements that you might need to be aware:
MX200G2:
https://www.cisco.com/c/en/us/products/collateral/collaboration-endpoints/telepresence-mx-series/eos-eol-notice-c51-739931.html?emailclick=CNSemail
MX300G2:
https://www.cisco.com/c/en/us/products/collateral/collaboration-endpoints/telepresence-mx-series/eos-eol-notice-c51-739932.html?emailclick=CNSemail
The recommended refresh will be Spark Room 55 or Spark Room Kit.
CE8.3:
https://www.cisco.com/c/en/us/products/collateral/collaboration-endpoints/telepresence-mx-series/eos-eol-notice-c51-739933.html?emailclick=CNSemail
You should start moving to CE 9.x, a lot of good stuff in the latest release:
https://www.cisco.com/c/dam/en/us/td/docs/telepresence/endpoint/software/ce9/release-notes/ce-software-release-notes-ce9.pdf
P40 camera related bundle:
https://www.cisco.com/c/en/us/products/collateral/collaboration-endpoints/telepresence-quick-set-series/eos-eol-notice-c51-739957.html?emailclick=CNSemail
https://www.cisco.com/c/en/us/products/collateral/collaboration-endpoints/telepresence-quick-set-series/eos-eol-notice-c51-739956.html?emailclick=CNSemail
MX200G2:
https://www.cisco.com/c/en/us/products/collateral/collaboration-endpoints/telepresence-mx-series/eos-eol-notice-c51-739931.html?emailclick=CNSemail
MX300G2:
https://www.cisco.com/c/en/us/products/collateral/collaboration-endpoints/telepresence-mx-series/eos-eol-notice-c51-739932.html?emailclick=CNSemail
The recommended refresh will be Spark Room 55 or Spark Room Kit.
CE8.3:
https://www.cisco.com/c/en/us/products/collateral/collaboration-endpoints/telepresence-mx-series/eos-eol-notice-c51-739933.html?emailclick=CNSemail
You should start moving to CE 9.x, a lot of good stuff in the latest release:
https://www.cisco.com/c/dam/en/us/td/docs/telepresence/endpoint/software/ce9/release-notes/ce-software-release-notes-ce9.pdf
P40 camera related bundle:
https://www.cisco.com/c/en/us/products/collateral/collaboration-endpoints/telepresence-quick-set-series/eos-eol-notice-c51-739957.html?emailclick=CNSemail
https://www.cisco.com/c/en/us/products/collateral/collaboration-endpoints/telepresence-quick-set-series/eos-eol-notice-c51-739956.html?emailclick=CNSemail